This article will guide you how to secure your files using VeraCrypt, a free and open source encryption tools and multi platform, works on Windows, Linux and Mac OS, available on GUI version and command line / console.
If you want to secure your file on Linux, you can use LUKS format, but it’s may did not work on Windows or Mac OS.
You can read How to create encrypted disk image with Linux LUKS format using Cryptsetup
Why Veracrypt?
VeraCrypt is a free disk encryption software based on TrueCrypt.
It adds enhanced security to the algorithms used for system and partitions encryption making it immune to new developments in brute-force attacks.
For example, when the system partition is encrypted, TrueCrypt uses PBKDF2-RIPEMD160 with 1000 iterations whereas in VeraCrypt we use 327670.
And for standard containers and other partitions, TrueCrypt uses at most 2000 iterations but VeraCrypt uses 655340 for RIPEMD160 and 500000 iterations for SHA-2 and Whirlpool.
It’s free and open source. More secure than TrueCrypt. Works on Windows, Linux and Mac OS. Works on hard drive or USB drive, extremely fast read and write.
You can check all great features on VeraCrypt’s Website.
How to install VeraCrypt on Linux
VeraCrypt support Centos 6, 7 and 8 GUI and console version. It’s also support Debian 9 and newer, Ubuntu 12 and newer, also openSuse.
Go to https://www.veracrypt.fr/en/Downloads.html and choose your version. In this example we use Console version.
Centos 6
# wget https://launchpad.net/veracrypt/trunk/1.24-update4/+download/veracrypt-console-1.24-Update4-CentOS-6-x86_64.rpm
# # rpm -ivh veracrypt-console-1.24-Update4-CentOS-6-x86_64.rpm
Centos 7
# wget https://launchpad.net/veracrypt/trunk/1.24-update4/+download/veracrypt-console-1.24-Update4-CentOS-7-x86_64.rpm
# rpm -ivh veracrypt-console-1.24-Update4-CentOS-7-x86_64.rpm
Centos 8
# wget https://launchpad.net/veracrypt/trunk/1.24-update4/+download/veracrypt-console-1.24-Update4-CentOS-8-x86_64.rpm
# rpm -ivh veracrypt-console-1.24-Update4-CentOS-8-x86_64.rpm
All Centos
# yum install -y fuse-libsCreating Encrypted Volume or Hard Disk using VeraCrypt on Linux
[root@serverdiary ~]# veracrypt -t -c
Volume type:
1) Normal
2) Hidden
Select [1]: 1
Enter volume path: /root/VeraCryptLinux
Enter volume size (sizeK/size[M]/sizeG): 5G
Encryption Algorithm:
1) AES
2) Serpent
3) Twofish
4) Camellia
5) Kuznyechik
6) AES(Twofish)
7) AES(Twofish(Serpent))
8) Camellia(Kuznyechik)
9) Camellia(Serpent)
10) Kuznyechik(AES)
11) Kuznyechik(Serpent(Camellia))
12) Kuznyechik(Twofish)
13) Serpent(AES)
14) Serpent(Twofish(AES))
15) Twofish(Serpent)
Select [1]: 1
Hash algorithm:
1) SHA-512
2) Whirlpool
3) SHA-256
4) Streebog
Select [1]: 1
Filesystem:
1) None
2) FAT
3) Linux Ext2
4) Linux Ext3
5) Linux Ext4
6) NTFS
7) exFAT
Select [2]: 2
Enter password:
Re-enter password:
Enter PIM:
Enter keyfile path [none]:
Please type at least 320 randomly chosen characters and then press Enter:
Characters remaining: 7
Done: 100.000% Speed: 297 MiB/s Left: 0 s
The VeraCrypt volume has been successfully created.If you want to encrypt entire disk for example /dev/sdb you can fill it when prompt Enter volume path: /dev/sdb
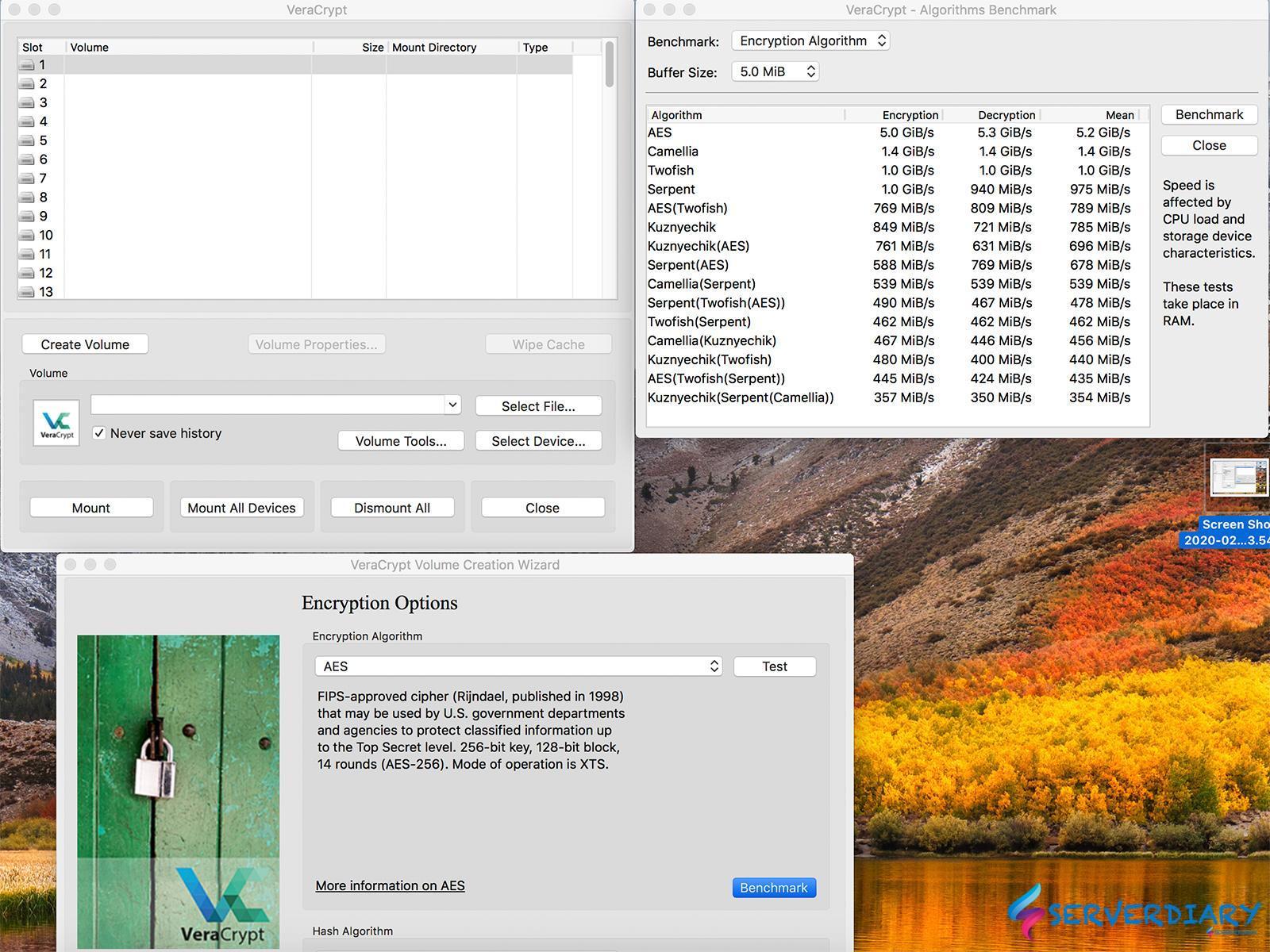
Encryption Algorithm we choose AES SHA-512. AES is fastest encryption. Picture below is benchmark speed Encryption Algorithm on Mac OS I7 woith 16GB RAM and SSD disk.
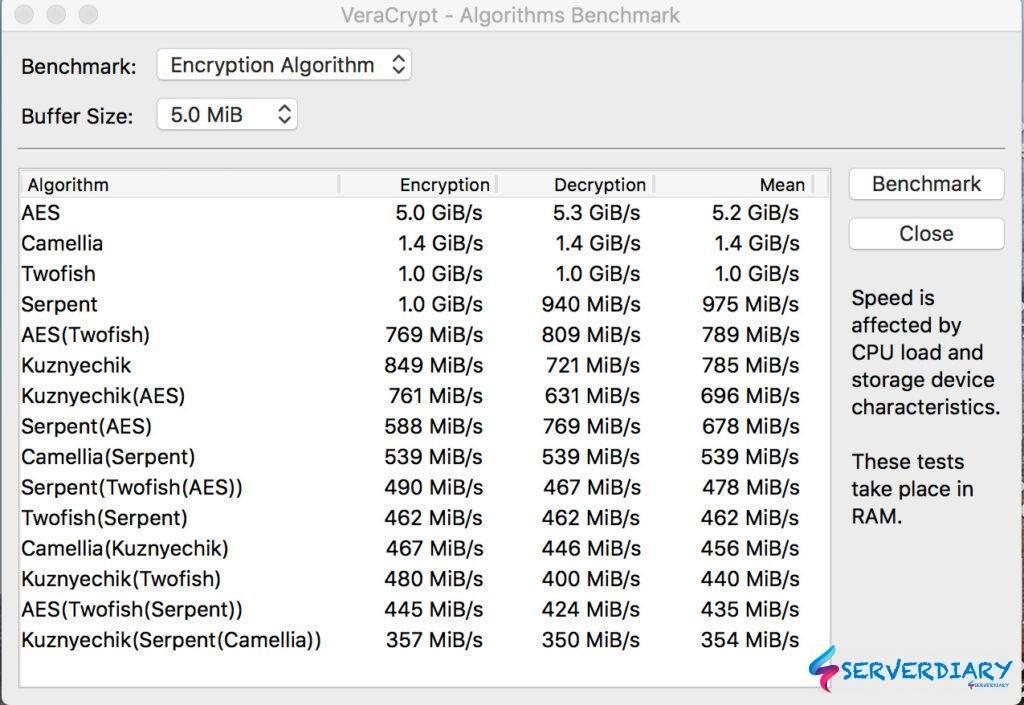
File system we choose FAT, because it can be used on Windows, Linux and Mac OS.
We did not put PIM. PIM is Personal Iterations Multiplier. You can customize the number of iterations when the head key of the encrypted disk is generated.
The larger the number of iterations, it will be longer to compute the header key, and slower the process of mounting the encryption disk.
If someone wants to use violent cracking to decrypt the “head” exhaustively, it will take a long time to try each time (also N iterations). When N is big enough, violent cracking becomes impossible.
Please note, if you set PIM, it’s like Two factor Authentication. You must remember password and PIM. Once you loose it, there is no way to get your disk or files back.
Mounting encrypted volume or disk on Linux
You can not directly mount encrypted disk using standar linux command. You must use veracrypt command to mount encrypted disk or encrypted volume.
[root@serverdiary ~]# mkdir -p /mnt/veracrypt
[root@serverdiary ~]# veracrypt /root/VeraCryptLinux /mnt/veracrypt
Enter password for /root/VeraCryptLinux:
Enter PIM for /root/VeraCryptLinux:
Enter keyfile [none]:
Protect hidden volume (if any)? (y=Yes/n=No) [No]:
root@serverdiary ~]# df -h
Filesystem Size Used Avail Use% Mounted on
devtmpfs 126G 0 126G 0% /dev
tmpfs 126G 136K 126G 1% /dev/shm
tmpfs 126G 3.0G 123G 3% /run
tmpfs 126G 0 126G 0% /sys/fs/cgroup
/dev/mapper/cl-root 442G 368G 75G 84% /
/dev/md127 1020M 376M 645M 37% /boot
tmpfs 26G 0 26G 0% /run/user/0
/dev/mapper/veracrypt2 4.8M 0 4.8M 0% /mnt/veracrypt
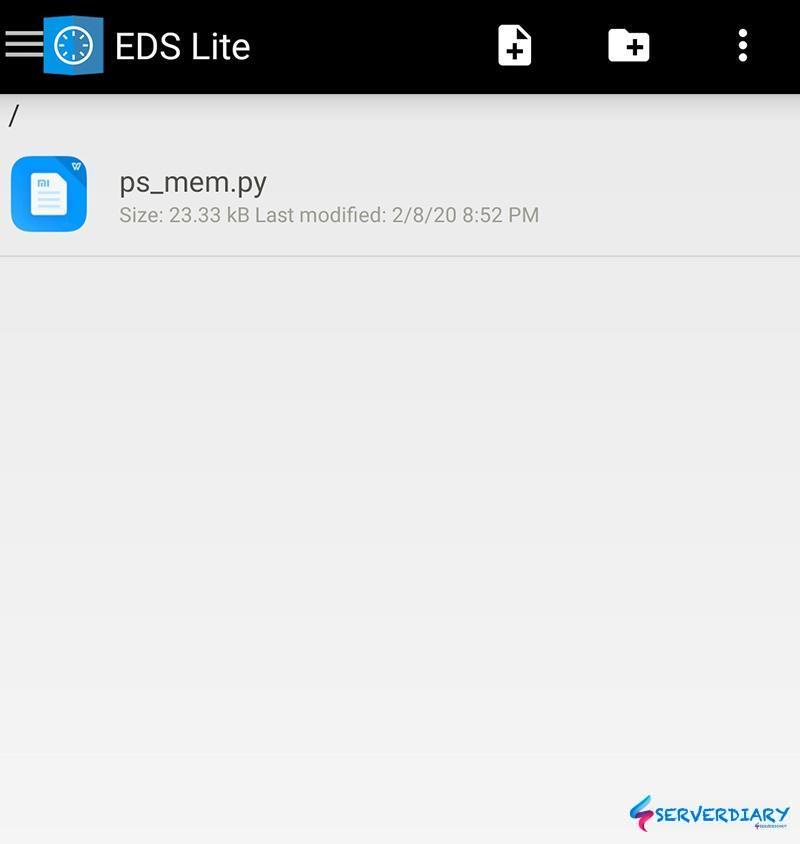
[root@serverdiary ~]# cp ps_mem.py /mnt/veracrypt/ps_mem.py
[root@cari ~]# ls /mnt/veracrypt
ps_mem.pyWe successfully mount volume and write file to mopunted VeraCrypt volume.
VeraCrypt VS Cryptsetup LUKS format speed benchmark
Check write speed of VeraCrypt Encrypted Volume, it’s very fast.
[root@serverdiary veracrypt]# cd /mnt/veracrypt
[root@serverdiary veracrypt]# dd if=/dev/zero of=test.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB) copied, 1.85724 s, 578 MB/sCheck write speed of Cryptsetup LUKS Format encrypted container
[root@serverdiary ~]# fallocate -l 5G encrypted_volume.iso
[root@serverdiary ~]# cryptsetup -y luksFormat encrypted_volume.iso
WARNING!
========
This will overwrite data on encrypted_volume.iso irrevocably.
Are you sure? (Type uppercase yes): YES
Enter passphrase for encrypted_volume.iso:
Verify passphrase:
[root@serverdiary ~]# cryptsetup luksOpen encrypted_volume.iso encVolume
Enter passphrase for encrypted_volume.iso:
[root@cari ~]# mkfs.ext4 /dev/mapper/encVolume
mke2fs 1.42.9 (28-Dec-2013)
Filesystem label=
OS type: Linux
Block size=4096 (log=2)
Fragment size=4096 (log=2)
Stride=0 blocks, Stripe width=0 blocks
327680 inodes, 1310208 blocks
65510 blocks (5.00%) reserved for the super user
First data block=0
Maximum filesystem blocks=1342177280
40 block groups
32768 blocks per group, 32768 fragments per group
8192 inodes per group
Superblock backups stored on blocks:
32768, 98304, 163840, 229376, 294912, 819200, 884736
Allocating group tables: done
Writing inode tables: done
Creating journal (32768 blocks): done
Writing superblocks and filesystem accounting information: done
[root@serverdiary ~]# mkdir -p /mnt/luksvolume
[root@serverdiary ~]# mount /dev/mapper/encVolume /mnt/luksvolume
[root@serverdiary ~]# cd /mnt/luksvolume/
[root@cari luksvolume]# dd if=/dev/zero of=test.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB) copied, 4.02094 s, 267 MB/sNow check write speed on /root directory
[root@serverdiary ~]# dd if=/dev/zero of=test.img bs=1G count=1 oflag=dsync
1+0 records in
1+0 records out
1073741824 bytes (1.1 GB) copied, 3.07795 s, 349 MB/sFrom simple benchmark above, VeraCrypt volume speed 578 MB/s, LUKS Format encrypted container speed 267 MB/s, and disk speed is 349 MB/s. So the winner is VeraCrypt volume.
Unmounting encrypted volume or disk on Linux
Do not use normal umount command to unmounting VeraCrypt volume.
[root@serverdiary ~]# veracrypt -d /mnt/veracryptIf you want to unmount all VeraCrypt volume, use this command:
[root@serverdiary ~]# veracrypt -dNow check all mounted file system.
[root@serverdiary ~]# df -h
Filesystem Size Used Avail Use% Mounted on
devtmpfs 126G 0 126G 0% /dev
tmpfs 126G 136K 126G 1% /dev/shm
tmpfs 126G 3.0G 123G 3% /run
tmpfs 126G 0 126G 0% /sys/fs/cgroup
/dev/mapper/cl-root 442G 368G 75G 84% /
/dev/md127 1020M 376M 645M 37% /boot
tmpfs 26G 0 26G 0% /run/user/0On Mac OS Big Sur, if you got an error mount_osxfuse: the OSXFUSE file system is not available (255)
# brew install --cask osxfuseAnd then added the permissions in the Settings > Security & Privacy > General to allow the extension
If it’s down not work, run this code:
# sudo kextutil /Library/Filesystems/osxfuse.fs/Contents/Extensions/10.12/osxfuse.kextIf all above step does not work, you may need to update FUSE to 4.0.4 https://osxfuse.github.io/2020/11/30/macFUSE-4.0.4.html
You may need need to update Veracrypt to the latest version: https://www.veracrypt.fr/en/Downloads.html
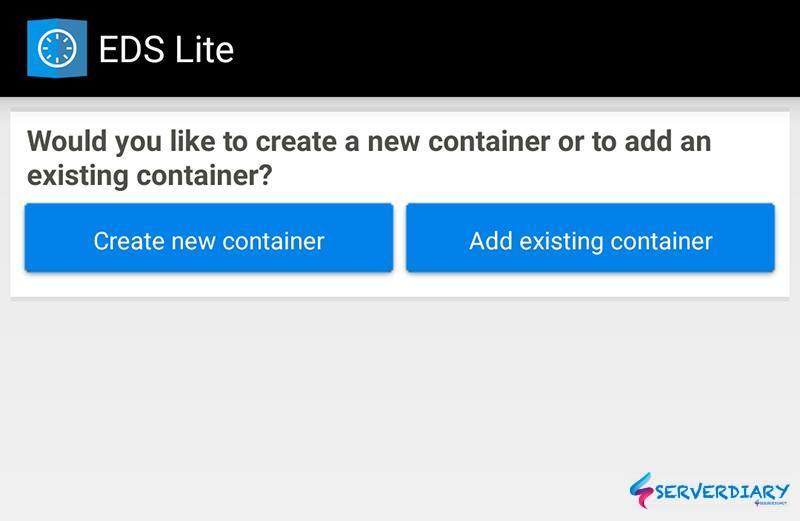
Create, Encrypt, Decrypt and Open VeraCrypt on Android
On android device you can use EDS Lite to Create, Encrypt, Decrypt and Open Veracrypt on Android.
Get EDS Lite on https://play.google.com/store/apps/details?id=com.sovworks.edslite
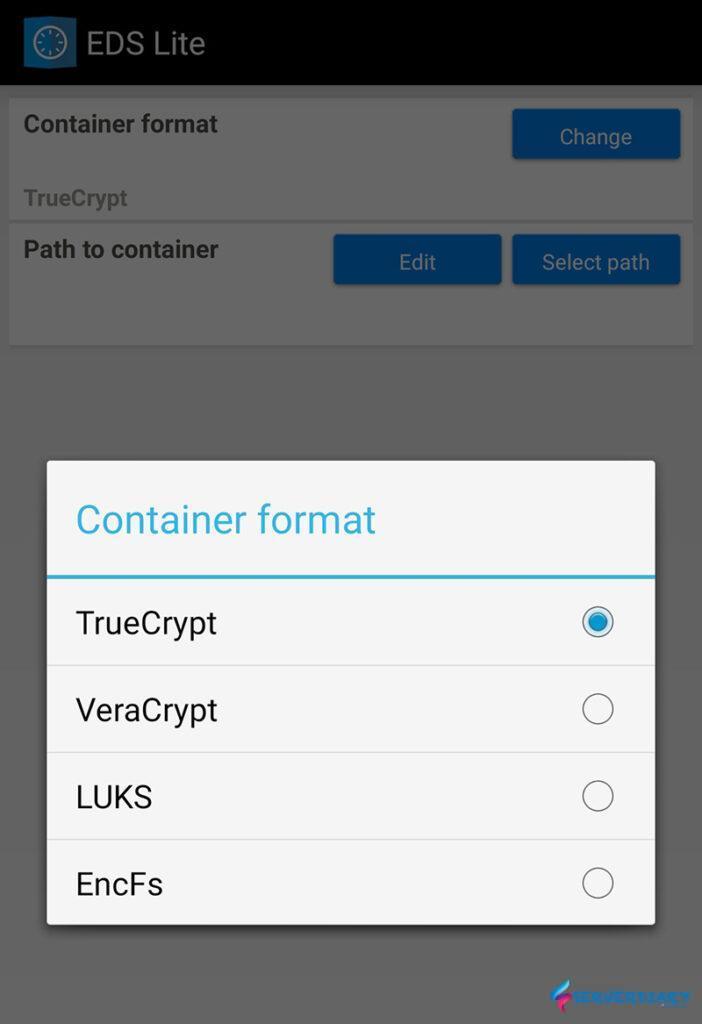
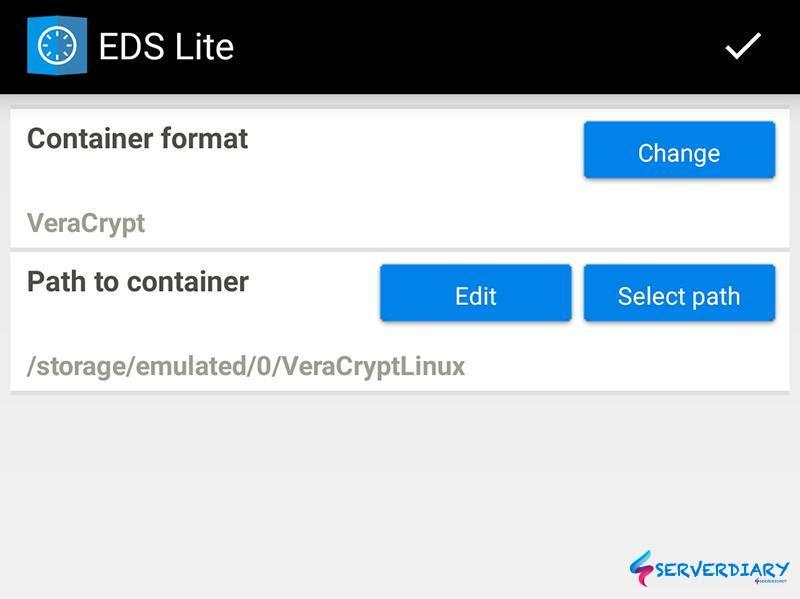
Click on manage containers then click Plus icon on top right. You can create new container or add an existing container.
On this article we choose add an existing container, that we create on Linux server (Centos 7).
and Disk Decipher for iOS and iPadOS