If you have sensitive data or file, you can make an iso image on Linux.
For example backup file, photo or even your source code, so no one can stole it.
Linux Unified Key Setup (LUKS) is a disk encryption specification created by Clemens Fruhwirth in 2004 and was originally intended for Linux.
LUKS is the standard for Linux hard disk encryption. By providing a standard on-disk-format, it does not only facilitate compatibility among distributions, but also provides secure management of multiple user passwords.
Also Read: Encrypt your files with VeraCrypt on Linux, Windows, Mac OS and Android
LUKS stores all necessary setup information in the partition header, enabling to transport or migrate data seamlessly.
The benefits of LUKS is compatibility via standardization, secure against low entropy attacks, support for multiple keys, effective passphrase revocation, and most important is it’s free.
Cryptsetup
Cryptsetup is a utility used to conveniently set up disk encryption based on the DMCrypt kernel module.
These include plain dm-crypt volumes, LUKS volumes, loop-AES, TrueCrypt (including VeraCrypt extension) and BitLocker formats.
You can read more about Cryptsetup project here.
On CentOs, Cryptsetup ins installed by default. But if not, you can manually install with command below:
# yum install cryptsetup-luksOn Ubuntu use this command to install;
# sudo apt-get install cryptsetupCreate an empty file and use Crypsetup to create LUKS container:
# fallocate -l 1024M encrypted_volume.iso
# cryptsetup -y luksFormat encrypted_volume.iso
WARNING!
========
This will overwrite data on encrypted_volume.iso irrevocably.
Are you sure? (Type uppercase yes): YES
Enter passphrase for encrypted_volume.iso:
Verify passphrase:Please note that must remember password. You can not get it back or use any forgot password, reset or remove password on LUKS container. So if you lost your password, you will never get your file on encrypted volume.
You need to decrypt your volume using crypsetup luksopen before you can format it.
# cryptsetup luksOpen encrypted_volume.iso encVolume
Enter passphrase for encrypted_volume.iso:The command above will map the file encrypted_volume.iso to the volume encVolume.
The volume encVolume will be available as /dev/mapper/encVolume. You can create file system for example Ext4, XFS or Fat.
# mkfs.ext4 /dev/mapper/encVolume
Filesystem label=
OS type: Linux
Block size=4096 (log=2)
Fragment size=4096 (log=2)
Stride=0 blocks, Stripe width=0 blocks
65408 inodes, 261632 blocks
13081 blocks (5.00%) reserved for the super user
First data block=0
Maximum filesystem blocks=268435456
8 block groups
32768 blocks per group, 32768 fragments per group
8176 inodes per group
Superblock backups stored on blocks:
32768, 98304, 163840, 229376
Allocating group tables: done
Writing inode tables: done
Creating journal (4096 blocks): done
Writing superblocks and filesystem accounting information: doneNow you can mount /dev/mapper/encVolume
# mkdir -p ~/backup
# mount /dev/mapper/encVolume ~/backupYou can put your files on ~/backup
To close your encrypted container, first you need to unmount file system.
Use this command:
# umount ~/backup
# cryptsetup luksClose encVolume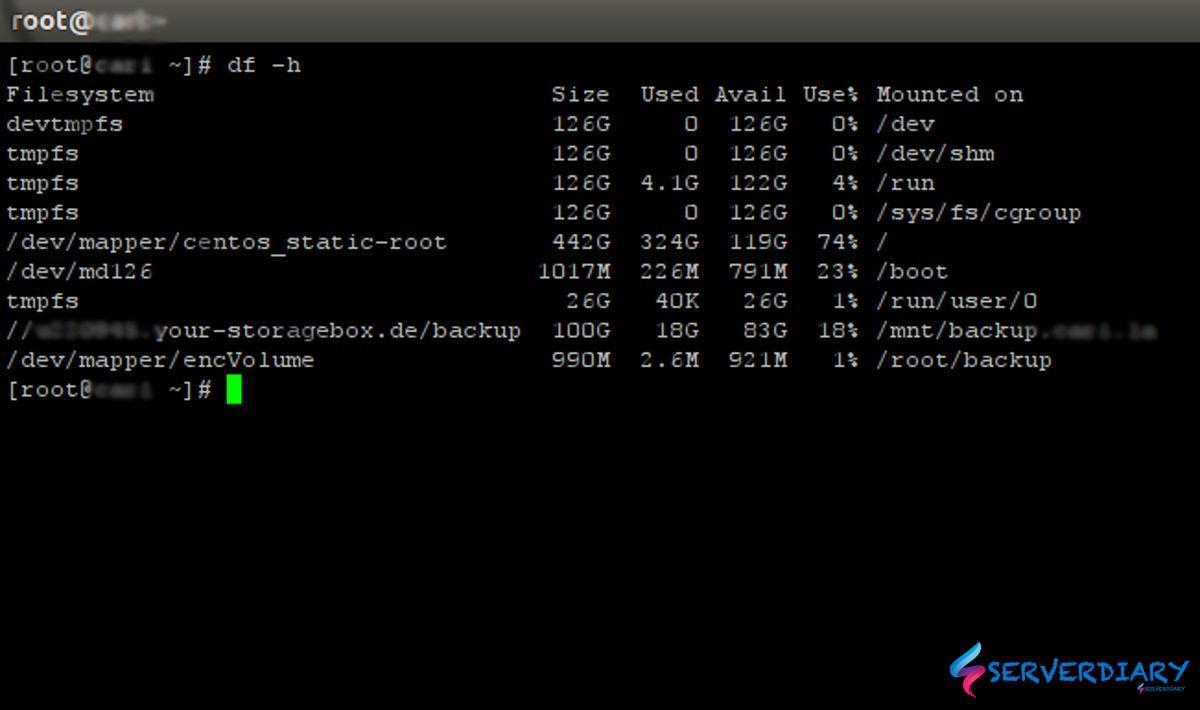
One thought on “How to create encrypted disk image with Linux LUKS format using Cryptsetup”